Integrate with GitLab
GitLab customers can retrieve secrets from HCP Vault Secrets using the vlt command-line interface (CLI).
Prerequisites:
- A Gitlab repository with permissions for viewing and modifying CI/CD job variables.
- An Admin role in an HCP Project
- An HCP Vault Secrets application and secret(s)
Service principal key
Open your web browser and log into the HCP Portal.
Click Access control (IAM). If you see the notification Modifying user permissions, click Go to org-name.
Click Service principals.
Enter a name in the Service principal name textbox and click Create service principal.
In the Keys pane, click Create service principal key.
Copy the Client ID and Client secret. These values will be used later to configure GitLab.
HCP organization and project ID
Navigate back to the project dashboard.
Click the HashiCorp logo in the top left corner.
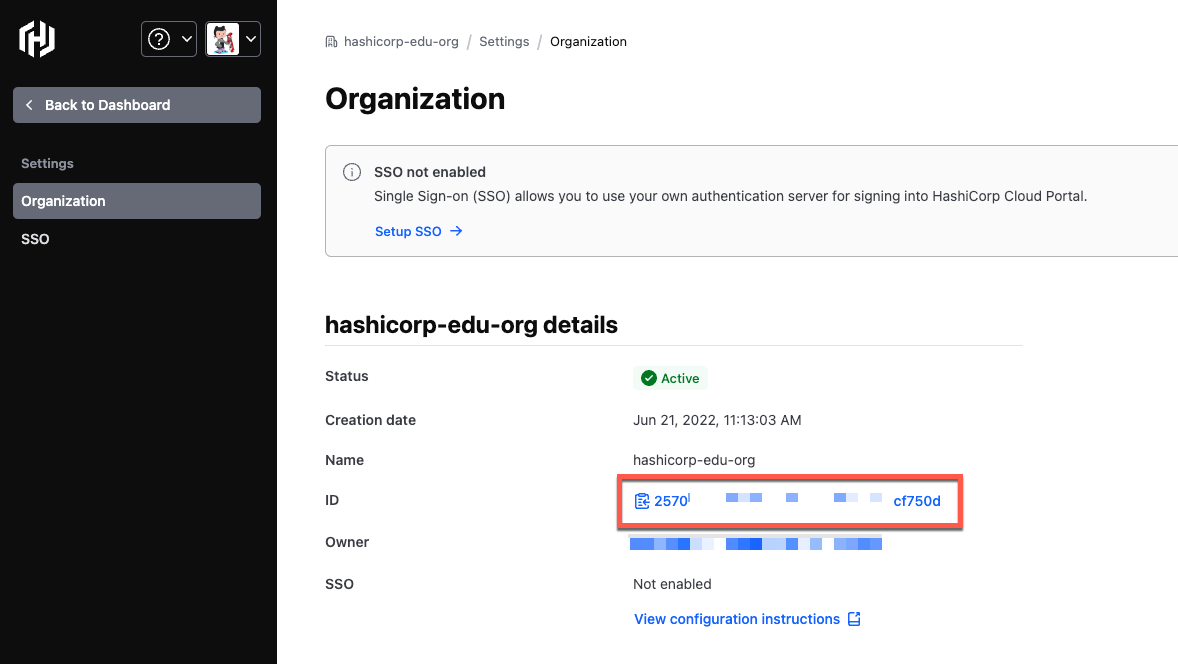
From the Organizations page, click the ellipses for the organization you want to connect to GitLab and select View.
Click Settings and copy the ID.
Click the Select a project menu and select the project you want to connect to GitLab.
Click Settings and copy project ID
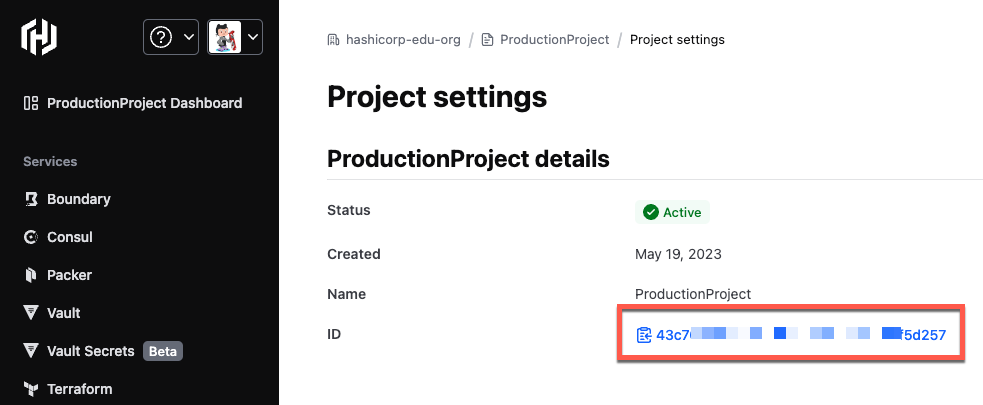
The organization ID and project ID values will be used later to configure GitLab.
Click Vault Secrets and copy the name of the application you want to use with GitLab. This value will be used later to configure GitLab.
GitLab
Log into GitLab and access the project you wish to configure for HCP Vault Secrets.
Expand Settings and click CI/CD.
Expand Variables.
Click Add variable.
In Key text box enter
VLT_ORGANIZATION_ID, in the Value field enter the org ID you copied from the HCP Portal, then click the Mask variable checkbox and click Add variable.Repeat the steps above to create variables for:
- VLT_PROJECT_ID
- VLT_APPLICATION_NAME
- HCP_CLIENT_ID
- HCP_CLIENT_SECRET
Configure pipeline
Update your .gitlab-ci.yml to install the vlt CLI and use vlt run to inject secrets as environment variables into any script or command.
Example: