Cluster networking
Newly deployed HCP Vault clusters are created with default network settings depending on the tier of the cluster. For Development tier clusters, public networking is the default and for all other tiers, private networking is the default. Proxy is enabled by default on all clusters and can be disabled in the cluster networking settings if desired.
To learn more about architecture of this network model, please refer to the HCP Data Plane documentation.
The cluster's network settings can be edited any time after a cluster is created to suit your networking requirements. To modify the cluster's network settings, navigate to the "Cluster networking" tab from the cluster's overview page. You can also view your cluster's configured networking settings from the overview page and obtain the public and/or private URL(s) to access the cluster.
The sections below provide information on the various networking options available for HCP Vault clusters.
Public connectivity
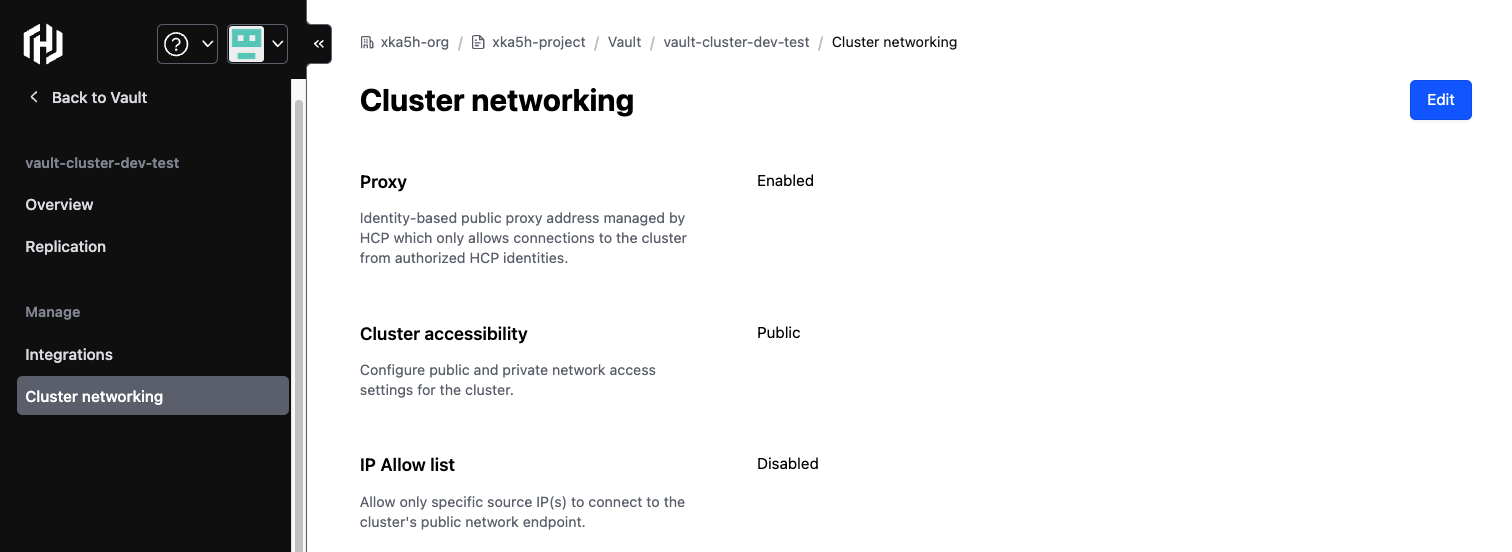
The public network accessibility option enables a publicly accessible endpoint where the cluster UI and API can be accessed. You can configure an IP allow list to limit the source IP range(s) that can connect to the cluster's public endpoint.
When the public network accessibility option is selected, private networking is also available and is covered in the section below.
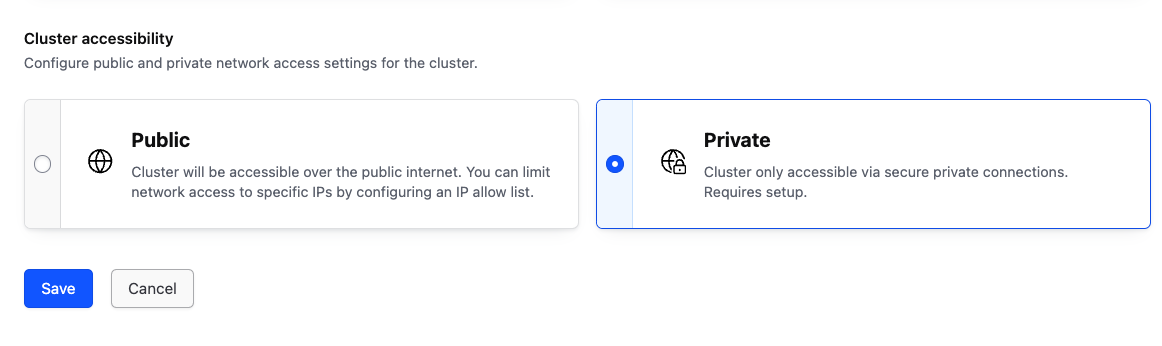
Private connectivity
Private networking with HCP Vault requires additional configuration within your AWS or Azure account depending on which cloud provider the cluster is deployed in.
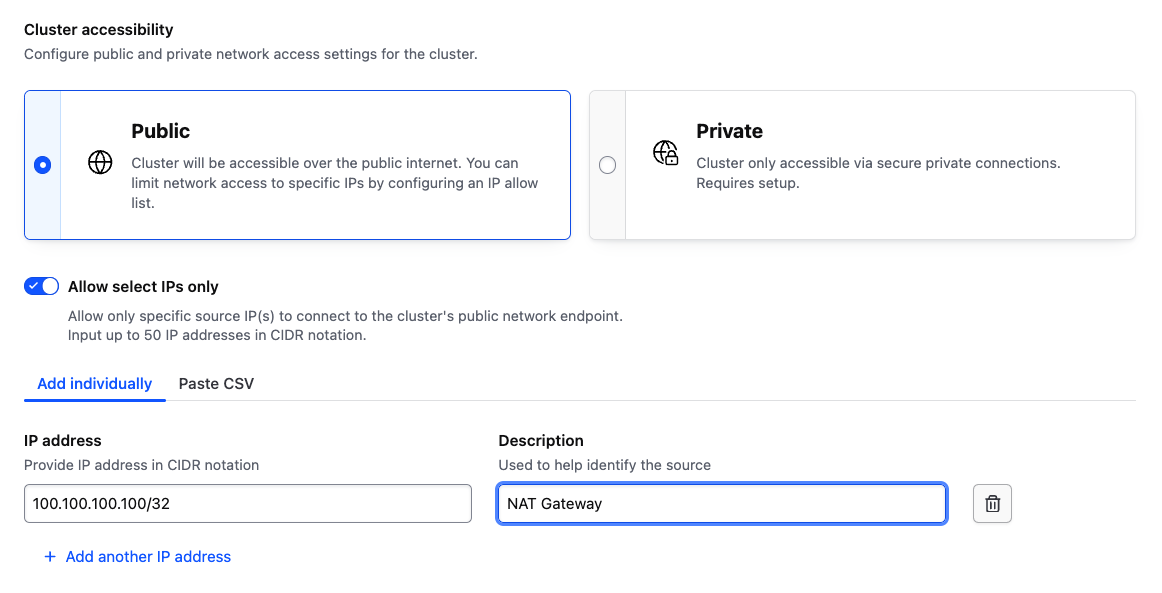
To use private networking only, you can explicitly set it within the cluster accessibility settings. Please note you will need to disable the proxy for the cluster separately if desired.
HCP Vault cluster networks can be privately peered or attached as a spoke to a hub network within an AWS or Azure account. Refer to the HashiCorp Virtual Network tutorials for steps on how to configure the available private connectivity options.
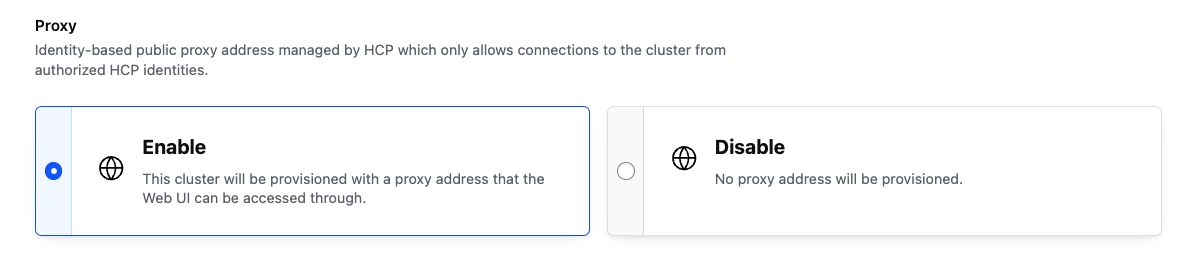
HCP Identity-Based Proxy
When enabled, the proxy option provides a publicly accessible proxy endpoint (managed by HCP) which only allows network connections to the cluster from authenticated and authorized HCP identities (users and service principals). This provides an identity-based method to secure connections to the cluster's UI/API publicly when IP allow list is not possible. This option can be useful for easy access to the cluster's UI for human administrators or connecting workloads from other SaaS platforms.
Access the UI using the cluster's proxy endpoint
With proxy enabled, a cluster configured with private network access can allow organization members access their HCP Vault clusters' UI directly from within the portal without needing to connect through the cluster's private network. This can be done using the "Launch web UI" button in the top-right corner of the cluster overview page.
Connect Vault CLI (requires Vault 1.16) to the HCP Vault cluster's proxy endpoint (Interactive)
Run vault hcp connect and follow prompts to choose the cluster you want to connect to. This command
may open a browser and prompt you to log into HCP if your machine is not already authenticated.
If you only have one HCP Vault cluster, the CLI will automatically connect to it.
Connect the Vault CLI (requires Vault 1.16) to the HCP Vault cluster's proxy endpoint (Non-interactive)
Create a service principal and key in your HCP organization with Viewer role. Copy the client id and client secret. Run the following command to set the CLIs context to connect to your HCP Vault cluster’s API. Please note the organization id and project id are UUIDs which can be obtained from HCP portal/url. The cluster id is the name of your cluster in HCP.
Once the Vault CLI is connected to the cluster's proxy endpoint, log into Vault via the vault login command using an appropriate auth method OR set a valid VAULT_TOKEN as an environment variable
to execute standard Vault CLI commands. You will also need to set a VAULT_NAMESPACE environment variable to the appropriate namespace
you want to log into and operate in. Run vault hcp disconnect to terminate the proxied connection from the CLI to the HCP Vault cluster.
Additional networking information
Network egress
HCP Vault cluster networks allow outbound TCP traffic to the internet which is required for certain secret engines and auth methods to work with external integration providers.
Cluster node IP addresses
HCP Vault cluster node IP addresses are dynamically assigned and it is recommended to always connect to the cluster's API/UI using the assigned DNS address.