What is HCP Vault Radar?
HCP Vault Radar is a product that automates the detection and identification of unmanaged secrets in your code so that security teams can take appropriate actions to remediate issues.
It scans for the following types of information:
- Secrets
- Personally identifiable information (PII)
- Non-inclusive language (NIL)
Once the scanning completes, the detected risks in your code are displayed by categories and ranks.
HCP Vault Radar helps you to eliminate the security vulnerabilities in your code.
Beta program
HCP Vault Radar is currently in private beta. If you would like to participate in the beta program, sign up here.
Who is HCP Vault Radar for?
HCP Vault Radar is for development teams and application security (AppSec) teams of all sizes, as well as enterprise information security (InfoSec) teams.
How HCP Vault Radar works
HCP Vault Radar scans connected code servers when a code server is initially added, when a commit is detected, and when pull requests are opened.
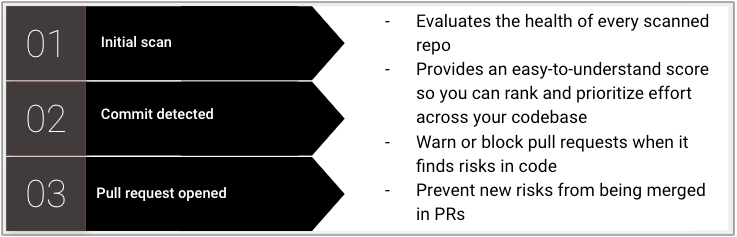
Use cases
HCP Vault Radar is used to identify risks in code, who has access, and where it goes:
Secrets
Passwords, keys, and other secrets in code are no longer secret when code is shared across teams, repos are made public, or when employees leave with copies of the code.
HCP Vault Radar identifies and helps eliminate secrets throughout the development workflow (in pull requests, and alert on commits to monitored repos), and make it easy to triage and mitigate secrets previously committed.
HCP Vault Radar’s deep scans identify secrets in git history, and can even identify active secrets so you know which ones are most important.
Personally identifiable information (PII)
Unlike secrets, personally identifiable information can’t be changed or rotated. As companies face growing liability for mishandling PII, finding and excising it from code is becoming a growing need.
HCP Vault Radar’s deep scans identify PII in git history, show teams the PII risk across their codebase, and help remediate. Just as with HCP Vault Radar’s secret detection tools, HCP Vault Radar can block PRs with PII, and alert teams any time PII is committed to monitored repos.
Non-inclusive language (NIL)
Companies and open source communities are both increasingly aware of the role inclusive language plays in attracting and retaining team members in all roles. Non-inclusive language creates both significant brand risks, as well as retention risks.
HCP Vault Radar’s tools help identify non-inclusive language throughout the development process, and guide teams to continuous improvement over time.